
Using Threat Modeling to Improve Compliance (TM Thursday)
Threat model Thursday is not just back, but live again!

Threat model Thursday is not just back, but live again!
The National Science Foundation is looking for information on needs for datasets.
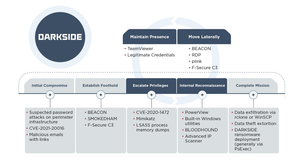
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can't delve into all of it.I did want to talk about one small aspect, which is the way responders talk about Darkside.
AppSec Pacific Northwest Conference is a free application security conference that will be held Saturday, June 19th. It is a virtual, online event sponsored by the OWASP chapters of Portland, Vancouver, and Victoria.

So there's some good news and some bad news in this story: 'Too Bad, Zuck: Just 4% of U.S. iPhone Users Let Apps Track Them After iOS Update'.
Apple has released ‘Device and Data Access when Personal Safety is At Risk’ and I wanted to explore it a bit.

“It depends on your threat model...”
Just stop.
If everyone agrees on what we should do, why do we seem incapable of doing it?
Expanding on the UK Government's ‘The Uk Code of Practice for Consumer IoT Security’ and how it aligns with Threat Modeling.
A bunch of people recently asked me about Robert Reichel’s post 'How We Threat Model,' and I wanted to use it to pick up on Threat Model Thursdays.
The timing of updates is not coincidental.

I get this question a lot: Can distributed/remote training work as well as in person? Especially for threat modeling, where there's a strong expectation that training involves whiteboards...

Developing a training program is hard, especially when it will be delivered remotely.

For Passover, we made a lamb and bitter greens pizza. Now, you may be saying to yourself that that’s wrong, but allow me to explain.